Security Settings
The following table lists the configurable Haivision EMS Security settings.
Note
Please contact your Network Administrator if you are unsure what to put in any of these fields or if you are unsure whether the setting is required on your network.
Setting | Description |
|---|---|
Appliance | |
FIPS | To enable FIPS cryptographic compliance on your system, toggle the FIPS button to On. Enabling FIPS cryptographic compliance applies cryptographic modules accredited under the U.S. Federal Information Processing Standard (FIPS) Publication 140- 2. Note To use FIPS mode, the CPU must include support for the RDRAND instruction. As a result, EMS VMware ESXi VMs can only run in FIPS mode on the following physical hardware:
|
High Security (STIG) Environment | To enable security hardening features for high-security environments, toggle this button to On. This setting includes:
These steps will all be applied when the STIG setting is enabled, and will be rolled back/canceled when the STIG setting is disabled. Note This complies with National Institute of Standards and Technology (NIST) Special Publication 800-53 (see https://nvd.nist.gov/800-53/ Rev 4). Important Only security professionals who understand the cipher support and requirements within their organization should change this setting. Some of these settings are not supported by Haivision Play Set-Top Box or by Google Chrome. The default list has been verified for broad acceptance, and should typically only be adjusted to mitigate new and critical vulnerabilities that may occur. |
Lock Session After | (High Security (STIG) Environment must be enabled) Type in the time period (in minutes) allowed for inactivity before an EMS session is locked (on all interfaces, console, ssh, and Web). |
Web Server | |
HTTP Port HTTPS Port | To configure the Web port for EMS:
|
SSL Protocols | To specify which TLS (Transport Layer Security) versions are accepted, click the checkboxes: TLS v1, TLS v1.1, TLS v1.2. |
SSL Ciphers | To specify which SSL Ciphers are accepted, select from the drop-down list or type in another cipher name: 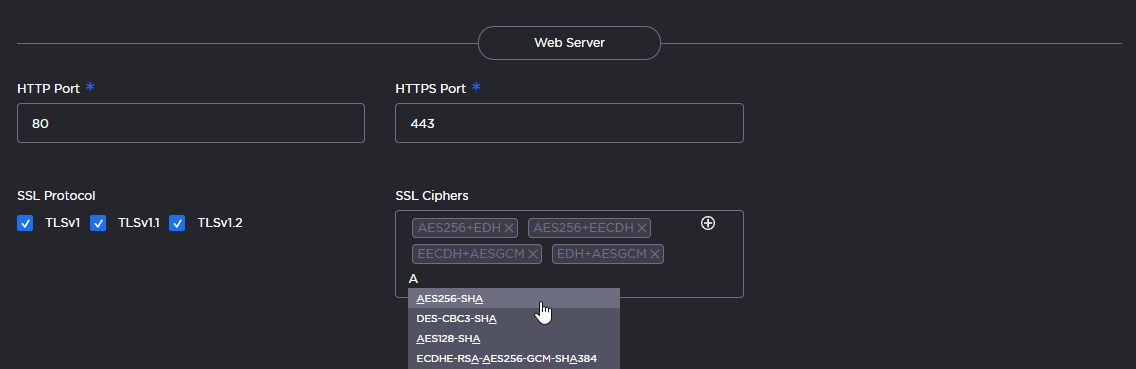 |
Advisory Notice & Consent Banner | |
Advisory Notice | When enabled, the banner will appear when users sign in (console, SSH and Web interface) and remain on the screen until the administrator acknowledges the usage conditions and takes explicit actions for further access. The banner is typically an advisory/warning notice to be displayed before the Sign In screen. To enable the banner (as shown in the text box), toggle the Advisory Notice button to On. Type or copy the banner text into the text box. |
